Deploy Windows faster on the factory floor by using the Full Flash Update (FFU) image format. FFU images allow you to apply an image of a physical drive, including Windows, recovery, and system partition information all at once directly to a different drive.
Integral 8GB Encrypted Drive With its impressive range of features, the Integral 8GB Crypto Drive tops our list of best encrypted drives available. This is a secure, water-tight device that holds all of your data and keeps it behind a 256-bit AES encryption code. The 256-bit AES encryption code is the industry standard. Jan 24, 2015 Memory will be upgraded from 4GB DDR3 to 8GB and HDD 250GB will be replaced by 250 Solid State drives. Current HDD are encrypted with Bitlocker and we want to clone the existing data to the new SSD. We try to 'suspend' encryption and clone with Acronis and Macrium but even when the image is done, the pc don't boot with the SSD. Encrypted backup is one of the easiest to use, most secure tools you can use to protect yourself. Let's take a closer look at what encrypted backup does and evaluate two different options: iTunes and Acronis True Image 2021. In This Article, We Will Be Covering: What is an encrypted backup; Why you should encrypt.
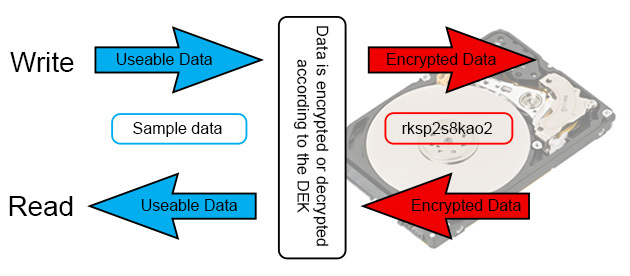
Configuration of Encrypted Hard Drives happens automatically in this environment when the Enhanced Storage component is added to the PXE boot image. During deployment, the TCGSecurityActivationDisabled setting in unattend.xml controls the encryption behavior of Encrypted Hard Drives.
Unlike the file-based WIM format, FFU is a sector-based file container that stores one or more partitions. Sector-based imaging means that FFUs take less time to deploy, but have larger files sizes than WIMs. See WIM vs. VHD vs. FFU: comparing image file formats for information about the differences between image formats.
Starting with Windows 10, version 1709, DISM has the ability to capture, deploy, and service FFUs, with the following limitations:

Deploy Windows faster on the factory floor by using the Full Flash Update (FFU) image format. FFU images allow you to apply an image of a physical drive, including Windows, recovery, and system partition information all at once directly to a different drive.
Integral 8GB Encrypted Drive With its impressive range of features, the Integral 8GB Crypto Drive tops our list of best encrypted drives available. This is a secure, water-tight device that holds all of your data and keeps it behind a 256-bit AES encryption code. The 256-bit AES encryption code is the industry standard. Jan 24, 2015 Memory will be upgraded from 4GB DDR3 to 8GB and HDD 250GB will be replaced by 250 Solid State drives. Current HDD are encrypted with Bitlocker and we want to clone the existing data to the new SSD. We try to 'suspend' encryption and clone with Acronis and Macrium but even when the image is done, the pc don't boot with the SSD. Encrypted backup is one of the easiest to use, most secure tools you can use to protect yourself. Let's take a closer look at what encrypted backup does and evaluate two different options: iTunes and Acronis True Image 2021. In This Article, We Will Be Covering: What is an encrypted backup; Why you should encrypt.
Configuration of Encrypted Hard Drives happens automatically in this environment when the Enhanced Storage component is added to the PXE boot image. During deployment, the TCGSecurityActivationDisabled setting in unattend.xml controls the encryption behavior of Encrypted Hard Drives.
Unlike the file-based WIM format, FFU is a sector-based file container that stores one or more partitions. Sector-based imaging means that FFUs take less time to deploy, but have larger files sizes than WIMs. See WIM vs. VHD vs. FFU: comparing image file formats for information about the differences between image formats.
Starting with Windows 10, version 1709, DISM has the ability to capture, deploy, and service FFUs, with the following limitations:
- The drive that an FFU is applied to has to be the same or larger than the drive it is captured from
- FFU captures of encrypted disks are not supported
- Captures of disks that have Volume Shadow Copy Service (VSS) enabled are not supported
- Splitting compressed FFUs is not supported
What you need to work with FFUs in Windows
To capture, deploy, and mount FFU images with DISM, you'll need to work in a Windows 10, version 1709 or later, or WinPE for Windows 10, version 1709 or later environment.
To capture and deploy FFUs using the instructions below, you'll also need:
- A Windows PC that has been generalized with Sysprep. We'll refer to this as the reference PC. For a walkthrough on how to create an image that's ready for deployment, see the OEM deployment of Windows 10 lab.
- A PC to deploy the FFU image to. We'll refer to this as the destination PC. The hard drive on this PC will be overwritten, so make sure you're using a PC that doesn't have any information you want to keep.
- The latest version of the ADK, from Download the Windows ADK
- Bootable WinPE media for Windows 10, version 1803 or later. See WinPE: Create USB bootable drive for instructions on how to create WinPE Media.
- Storage
USB storage, formatted as NTFS with enough space to save the FFU. 16 GB is enough space to store an FFU of a basic Windows image. You can use the same USB drive for WinPE and storage if you follow the instructions for creating a multipartiton USB drive. For best performance, you want to maximize I/O between where your FFU is stored and the destination PC. For best performance use a USB 3.0 drive to store the image, and an internal SSD for the destination device.
or
Network storage where you can keep your FFU image. For optimal performance, use a 1 Gb or faster network.
Capture an FFU
Boot the reference PC using WinPE bootable media.
Identify the drive to which you'll be capturing the image from. You can use diskpart, or add Windows PowerShell support to WinPE and use Get-Disk for scriptability and more complex setups such as a server with multiple disks.
The output will list your drives. Make a note of the disk number in the
Disk ###column. This is the value that you'll use when capturing your image.Use DISM to capture an image of all the partitions on the physical drive. For disk X:, the string used with
/capturedrivewill look like this:.PhysicalDriveX, where X is the disk number that diskpart provides. For example, to capture Disk 0, you'd use/CaptureDrive:.PhysicalDrive0.For more information about PhysicalDrive X, see CreateFile function.
To see command line options for capturing FFUs, run
dism /capture-ffu /?or see DISM Image Management Command-Line Options. Note that you shouldn't have to specify a PlatformID when capturing a desktop image.The following command captures an FFU image of PhysicalDrive0 called WinOEM.ffu. The /name and /description arguments allow you to set information about your image. This information is displayed when you use
dism /get-imageinfo. /name is required, /description is optional.This command also gives a name and description to the FFU image. Name is a required parameter.
Deploy Windows from WinPE using an FFU
Boot your destination PC to WinPE.
Connect a storage drive or map the network location that has your FFU file and note the drive letter, for example, N.
Identify the drive to which you'll be applying the image:
Note the drive number in the Disk ### column.
Apply the image to the cleaned drive. Here, we're applying n:WinOEM.ffu to Disk 0.
To see the commands available with /apply-ffu, run
dism /apply-ffu /?or see DISM Image Management Command-Line Options.
Capturing and applying FFUs on differently-sized drives
The FFU format captures the partition layout. If the reference PC and destination PC hard drives may be different sizes, use this strategy to make sure your Windows partition is as large as it can be:
On the reference PC, install Windows with no recovery partition, and set up the Windows partition as the final partition on the drive. To set this up, use Windows Setup or a deployment script.
Capture the FFU.
On the destination PC, deploy the FFU. For larger drives, there will be unused space at the end.
Using Diskpart, expand the Windows partition to fill the empty space.
Then, shrink the Windows partition to make room for the recovery partition.
Configure your recovery partition.
Example, using Sample scripts: create recovery partition.
Mount an FFU for servicing
You can use DISM to mount FFU images for servicing. Like with other image formats, you can mount and modify an FFU before committing changes and unmounting. Mounting an FFU for servicing uses the same /mount-image command that you use for mounting other image types. When mounting an FFU, you'll always use /index:1 when mounting.
Unlike WIM images, FFU images get mounted as virtual hard disks. Files appear in the specified mount folder, but since FFUs can contain more than one partition but only have one index, DISM maps only the Windows partition from the mounted FFU to the mount folder.
To mount an FFU
Open a Command Prompt as administrator.
Mount the image using
dism /mount-image. This example mounts D:WinOEM.ffu to C:ffumount:To see available command line options for
/mount-imagerundism /mount-image /?or see DISM image management command line options.Service your image. For example, to enable the legacy components feature:
To see available options, run
dism /image: /?orUnmount your FFU image and commit or discard changes. If you use /commit, your changes will be saved to your FFU file.
To unmount your FFU and commit changes, you'd use
/unmount-imagewith the/commitoption:If you decide to not keep the changes you've made to the FFU, you can use
/unmount-imagewith the/discardoption:
Related topics
Elcomsoft Encrypted Disk Hunter
Imaging Encrypted Drives App
Elcomsoft Encrypted Disk Hunter is a free, portable command-line tool to quickly discover the presence of encrypted volumes when performing live system analysis.
Imaging Encrypted Drives Drive
Multiple Windows, Linux and macOS full-disk encryption tools are supported including TrueCrypt/VeraCrypt, all versions of Microsoft BitLocker, PGP WDE, FileVault2, and LUKS. The tool must be launched with administrative privileges on the live system being analyzed. If an encrypted volume is detected, a further investigation of a live system might be needed to preserve evidence that could be lost if the computer were powered off.

